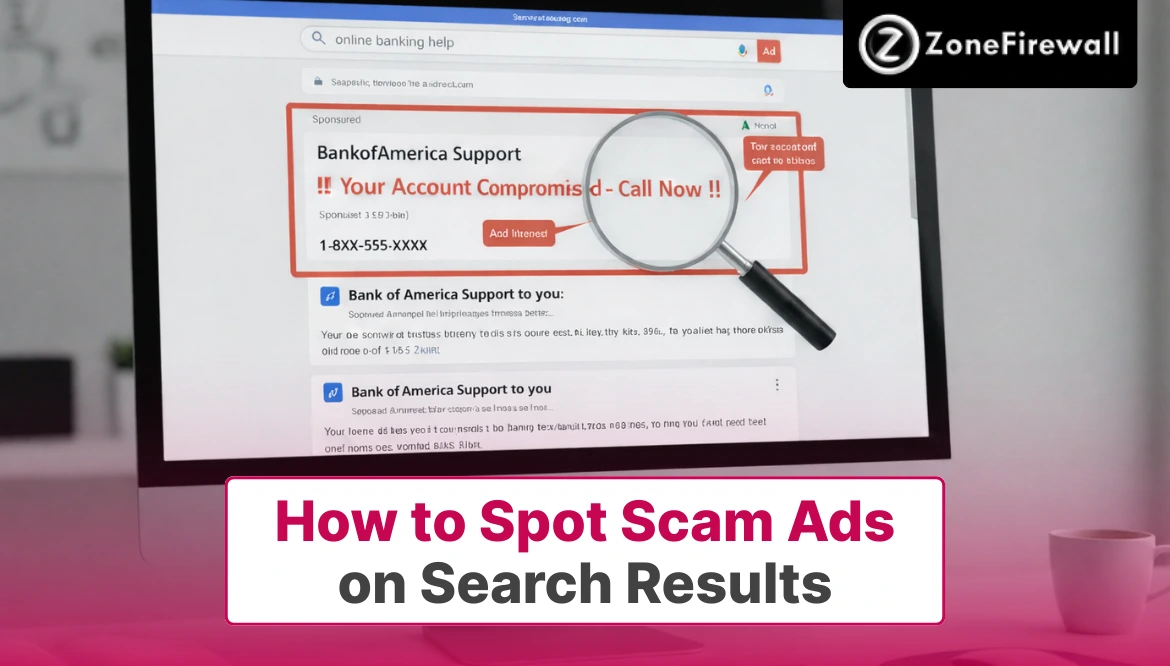
How to Spot Scam Ads on Search Results
Search engines are often the first place we go when we need help, want to buy something, or look for customer support. Unfortunately, scammers know this too.
Need immediate technical help? Provide your details below and our team will connect you with an available technician.

Search engines are often the first place we go when we need help, want to buy something, or look for customer support. Unfortunately, scammers know this too.

Autofill features save time by filling in usernames, addresses, and payment details automatically. From browsers to mobile apps, many people rely on autofill every day without thinking twice.

Login alerts are meant to protect accounts, but many users ignore them or misunderstand their value. Criminals know this. They look for weak, delayed, or poorly designed login alerts to slip into accounts without raising concern.

Contact requests feel harmless. A name appears, a profile photo looks normal, and a short message feels polite.

Security audits are meant to protect systems, data, and users from harm. Businesses and individuals trust audits because they promise safety, checks, and improvements.

Customer feedback plays a big role in how people choose products, services, and businesses. Before buying or signing up, most users read reviews to feel confident. Criminals understand this behavior very well.

Storing and sharing files online has become a normal part of daily life. From personal photos and bank documents to work files and login details, a lot of sensitive information now lives on the internet.

Online shopping has made life easier, but it has also opened the door to new types of scams. One of the most common and convincing tricks today is the fake refund scam. These scams target shoppers when they are already thinking about returns, delays, or payments.
.webp)
Text messages feel personal and direct, which makes them a powerful tool for scammers. Phishing through text messages, often called smishing, has increased sharply in recent years. These messages pretend to come from trusted sources such as banks, delivery services, government offices, or well-known brands.

Email scams continue to fool people every day. Many scams do not look suspicious at first glance. The real trap often starts with the subject line. Scammers carefully choose words that push fear, curiosity, or urgency. One click can lead to stolen details, financial loss, or device issues.






Webcams are everywhere - on your phone, PC, laptop, and so on. They allow you to capture photos and record videos.















Dear Valued Clients,
We’re excited to announce an important update to the way we offer our services at ZoneFirewall LLC. Starting October 1, 2025, we will be transitioning from custom pricing to two fixed service plans—designed to simplify your experience and bring more clarity to our pricing structure.
Perfect for quick, on-demand support, this plan includes:
What You Will Get
Perfect for quick, on-demand support, this plan includes:
What You Will Get
This shift is designed to:
If you’re currently on a custom plan, you’ll continue under the existing terms until your agreement ends. After that, you can choose the plan that best suits your needs.
We’re here to help! Reach out by phone at +1-877-219-0446 or email us at billing@zonefirewall.co.uk with any questions.
Thank you for your continued trust in ZoneFirewall LLC. We look forward to supporting you with these new, streamlined service options.
Sincerely,
The ZoneFirewall LLC Team
zonefirewall.co.uk
+1-877-219-0446
billing@zonefirewall.co.uk